PRIVATE NETWORK LIFE CYCLE
Various deployment options, stringent KPI requirements and the need for security make the deployment of a 5G private network quite complex. Success requires a holistic view of the network life cycle from design validation through operation.
Step 1: Validation and Conformance of Industrial Devices
Designing a 5G private network starts before designing and installing the real network, beginning with the design, validation and conformance testing of industrial devices. Mostly for Industry 4.0 applications, 5G private network devices create new challenges because they feature special qualities and are often integrated into industrial equipment. These devices are evolving and becoming more complex. For example, future factory robotic arms will have multiple cellular connections to increase positioning accuracy and versatility, and the embedded cellular devices will connect to the 5G base station directly or through a gateway (see Figure 6).
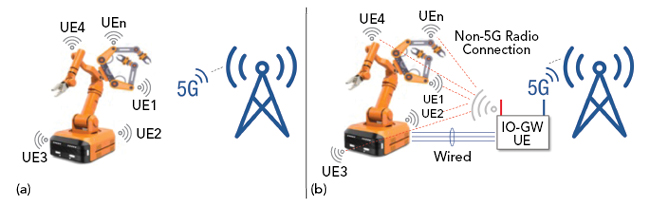
Figure 6 Robotic arm with embedded cellular connected to a 5G base station: directly (a) and through a gateway (b). Source: 5G-ACIA.
The unique capabilities and growing complexity of industrial devices and their integration requirements require testing for:
- Cellular integration of the module in the industrial device
- Connectivity, reliability and stability
- Functionality and performance
- Conformance to 3GPP and operator standards
- Security
- TSN/5G integration
- Ultra-reliable and low latency communications (URLLC)
- High positioning accuracy.
In addition to the devices, the RAN and core equipment require validation for functionality, performance, reliability and interoperability; the equipment must also meet industry standards, security and TSN/5G integration requirements.
Factory Channel Modeling
After the specifics of the industrial devices, the characteristics of the industrial network environment must be considered. Factories use metal and high speed rotating machines, with many obstructions to RF in a small area. These surfaces increase signal reflection, refraction and fading (see Figure 7). Validating industrial devices with signal propagation models, as close as possible to the actual factory channel models, is important to obtain high performance of the private network when fully implemented.
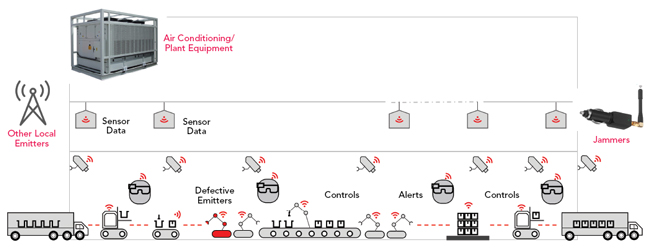
Figure 7 Potential sources of interference in a factory.
Step 2: Network Design & Planning
The next phase starts the network development with the design and installation of a physical network. The steps comprise:
- Site surveying, radio planning and spectrum clearance, including interference and jamming assessment
- Deployment modeling, slicing and isolation
- Designing the MEC
- Over-provisioning and optimizing.
Spectrum clearance is an important area during design and planning to ensure that no other system nearby will use the same frequencies allocated to the private network. Ensuring adequate RAN performance requires verifying the spectrum and identifying potential sources of interference, such as local electrical and plant equipment, strong signals from nearby emitters and defective equipment. It is also important to identify potential sources of jamming. Eliminating, or at least minimizing interference and removing jamming sources is essential to and a necessity for legal reasons.
The network design of the private network will use one of the models shown in Figure 1: an isolated network sharing no resources with the public network, a hybrid network sharing some resources or a dedicated 5G slice from a public operator. To avoid congestion at peak loads, over-provisioning the network should be considered. Avoiding network congestion includes designing the mobile edge cloud data center for the peak workload keeping in mind computing, networking and storage needs.
Step 3: Network Deployment
Once the design is complete, the process shifts to acceptance and performance testing. Site acceptance testing helps validate the network installation and must include the RAN or open RAN, 5G core and MEC, as well as spanning the end-to-end network. Functional testing should include isolated and interconnected network elements, as well as the end-to-end network with all elements integrated.
Site acceptance testing for the RAN includes functional testing for connectivity and standards conformance; performance testing for coverage, speed, latency and other quality of service (QoS) aspects; availability, reliability and stability; and over-the-air signal verification. Core network testing encompasses functional testing for connectivity and standards conformance; performance testing for coverage, speed, latency, positioning and other QoS aspects; and availability, reliability and stability testing. End-to-end testing comprises interoperability testing; functional testing for connectivity and standards conformance; performance testing for coverage, speed, latency and other QoS aspects; availability, reliability and stability testing; and security testing.
Performance testing needs to assess all the devices, the RAN, core network and MEC, as well as the end-to-end performance of the network. While testing interoperability is particularly challenging with a complex end-to-end network, continuous integration and continuous deployment (CI/CD) tools can automate much of the testing. Expertise in test methodologies also helps accelerate interoperability testing.
Security — The data generated in a factory must remain secure and should not leave the data center, except as needed by the factory owners. The following domains should be tested for vulnerabilities:
- User equipment (UE), as the devices are the first and last line of defense against cyberattacks
- Core network, including network access (NAS/authentication for secured UE attachment to the 5G network), the network domain (edge core perimeter defense and security enforcement), the application domain (encryption/decryption and deep packet inspection for security enforcement) and the service-based architecture domain (security against fuzzing and volumetric denial of service attacks)
- Open RAN, including the security of disaggregated and virtualized RANs
- Edge cloud for the security of applications and critical data applications and critical data.
MEC — In the context of MEC, verifying that the data center infrastructure meets the storage, network and computer power requirements is important. The network function virtualization infrastructure (NFVi) must be tested to ensure that it meets the performance needs. Data processing and storage should be inside the factories or close proximity, with results of the analysis sent to the users or machines for swift action. This requires a high performance cloud.
For example, in vision-based quality analysis, a camera in an assembly line may take photos under various lighting conditions, and the images are uploaded into the mobile edge cloud where an application processes them using AI to assess product quality. A robot on the factory floor then accepts or rejects the product based on the results. All these tasks must occur quickly.
Step 4: Network Operation and Optimization
Operation is the last phase of the private 5G network life cycle. During this stage, network monitoring is important to assure security, assess network and cloud performance, monitor critical and non-critical communications and identify interference and jamming.
The number of subscribers on a private network is much lower than on commercial networks, however, ensuring data security is critical. This drives the need for an end-to-end life cycle strategy (see Figure 8).
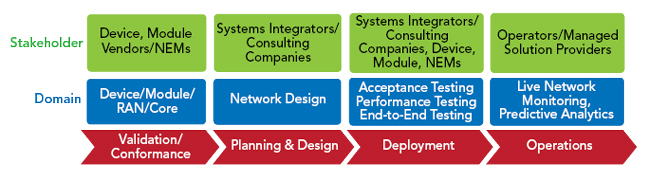
Figure 8 5G private network life cycle.
SUMMARY
5G private networks present many challenges to manufacturers and their partners. Successful deployment starts much earlier than the network design and planning stage, with the development of industrial devices and network elements, and continues during network operation. Several network architectures are feasible; choosing one requires careful consideration of the use case, the available expertise in-house and the manufacturer’s business strategy. The need for MEC and TSN are also important requirements affecting network design. Whichever configuration is selected, security must be embedded throughout the private network’s design and deployment phases, from device validation to ongoing network monitoring.
References
- ABI Research, “Monetizing 5G Edge Networks,” Application Analyst Report AN-5285, 3Q 2021.
- ABI Research and Nokia, “Enterprise Digital Transformation Through Industry 4.0,” Web, onestore.nokia.com/asset/207305.

