As vehicles become more automated, security issues in automotive systems such as radar and dedicated short-range communication (DSRC) must be thoroughly examined. This article provides an overview and comparison of the inherent security flaws in automotive radar and DSRC technologies. Existing implementations of automotive radar are vulnerable to spoofing attacks from third parties, potentially resulting in fatal accidents. While DSRC exhibits inherent resilience to spoofing attacks, it is still susceptible to similar types of attacks used against traditional Wi-Fi. This article concludes with a discussion on the motivation for combining radar and DSRC into a joint system, and an overview of the potential consequences of an insecure vehicular system.
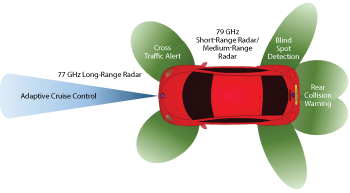
Figure 1 Uses of mmWave radar in vehicles.
Many new radio frequency (RF) technologies are being deployed to make driving safer and more automated. Automotive radar is one such technology, where RF signals are used for adaptive cruise control, forward collision warning or blind spot detection. Wireless communication used by cars is also increasing. For example, many models support mobile Wi-Fi hotspots. Going forward, many vehicles will be connected using dedicated short-range communication (DSRC), a wireless communications standard that enables reliable data transmission in active safety applications. Each technology, however, comes with its own security risks. Even isolated security breaches could have a dramatic impact on consumer confidence, resulting in the discontinuation of such technologies. In this article, we present an overview and comparison of security risks associated with both automotive radar and DSRC systems. We make a suggestion about how the industry should respond to these known threats, for example, through joint radar and communication. Furthermore, we describe an instance of a past successful attempt to hack a vehicle and speculate on future hacking attempts.
SECURITY RISKS OF AUTOMOTIVE RADAR
The majority of automotive radars on the market today operate in the millimeter wave (mmWave) band.1 Figure 1 illustrates the major uses of mmWave radar in vehicles. Specifically, long-range radar operates from 76 to 77 GHz, medium-range radar operates from 77 to 81 GHz and short-range radar (previously in the 24 GHz band) operates from 79 to 81 GHz. Additionally, research on leveraging the IEEE 802.11ad standard for automotive radar at 60 GHz is currently being conducted at The University of Texas at Austin.2
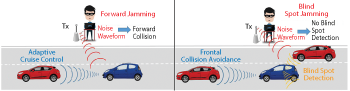
Figure 2 Two types of jamming attacks.
The types of attacks on vehicular radars are slightly different than the ones targeting radars in other settings due to the mobile nature of vehicular networks. There are three principle attacks (i.e., intentional disruption of a vehicular system by a third-party) on automotive radar.3,4 Jamming is the transmission of RF signals to interfere with a radar by saturating its receiver with noise. Spoofing is the replication and retransmission of transmitted radar signals in order to provide false information to the receiver. Interference is the intentional or unintentional modification or disruption of a radar signal by unwanted signals, such as signals from different automotive radars. Note that although some forms of interference may not be considered attacks, we will discuss their implications for the sake of completeness.
Jamming
Figure 2 illustrates two different types of jamming attacks. Both forward and blind spot attacks can effectively disable the functionality of vehicular radar, leaving the driver vulnerable to a collision. Due to the long-term use of mmWave radars in military applications, there is an extensive history of research on jamming in mmWave radars.3,5 A simple jamming technique uses a tunable scanner to determine the frequency of a radar signal and generates a jamming signal at the same frequency, disrupting the target radar’s receivers.6 More advanced jamming techniques may employ jamming signals with specific polarizations to more effectively disrupt the target radar’s antennas.7,8
Automotive mmWave radar has a limited range due to small wavelengths and the inability to consistently pass through solid objects.9 Most radars overcome this with a substantial amount of directivity, which also provides more resistance to jamming compared to systems that operate at lower frequencies. Additionally, since the purpose of jamming is to deny service, it is moderately difficult to conduct an effective jamming attack on an automotive radar in a highly mobile environment. If the jammer is in a static location, even a successful breach will disrupt an automotive radar for only as long as the target is in range, which may be a matter of just a few seconds in a highly mobile environment (i.e., highway). Although the potential consequences of losing a few seconds of operation are significant (i.e., loss of collision detection for that time frame), it is incredibly difficult for a malicious attacker to predict exactly where and when the jammer needs to operate to cause an accident. As a result, the attacker is limited to jamming in environments with low mobility (i.e., downtown areas) and does not have the ability to focus an attack on a single radar system.
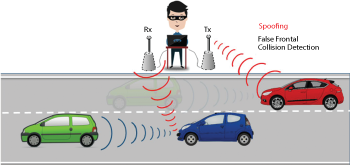
Figure 3 mmWave spoofing attack.
If the jammer is mobile, much more damage may be inflicted. A jammer located on a vehicle that is currently following the target radar may be able to continuously jam it. Executing a continuous jamming attack requires two major components in order to be successful. First, the vehicle with the jammer must stay within a certain range of the target vehicle without attracting suspicion. Second, the operation requires a jammer that can accurately scan the wireless channel in a highly mobile environment, which is notably complex. To perform the attack, the jammer must be able to scan the target vehicle from any direction and distinguish its radar signals from any other wireless signal. It must also transmit a strong jamming signal in the direction of the target vehicle.
Although jamming attacks have the potential to induce major collisions, current jammers do not have the necessary adaptability to perform in a highly mobile environment, making it very difficult for malicious attackers to target a single vehicle.
Spoofing
Automotive mmWave radars are known to be susceptible to spoofing. Figure 3 illustrates an attack that has the potential to cause the radar to report false information and greatly increases the risk of a collision. A spoofing demonstration was conducted by Chauhan,10 where the subject radar reported distances significantly shorter than the actual distance to the target. In addition, distance and velocity-falsifying attacks on commercial automotive radars have been shown to be feasible.10,11
Automotive radar exploits a specific signal structure that performs well as a radar signal (i.e., has strong autocorrelation properties) but exhibits no inherent authentication capability, leaving it vulnerable to spoofing attacks. Without a means for checking signal integrity, the receiver is unable to verify the spoofed sequences, making it possible to analyze and replicate the signal. Unlike a jamming attack, a spoofing attack is designed to confuse the victim. Ideally, it needs only to breach the vehicle radar for a short period of time to severely influence its behavior, potentially causing it to stop, change direction or, in the worst case, collide. A successful spoofing attack can therefore have a devastating effect on automotive radars in today’s market.
Despite this vulnerability, there have been no publicized reports. We believe that this is due to the relatively high implementation complexity inherent in the design of an effective and robust spoofing system. Overall, however, spoofing is the primary security concern for automotive radar due to its feasibility and potential consequences.
Interference
Most automotive radars employ frequency-modulated continuous wave (FMCW) waveforms.12 They exploit small shifts in signal frequency by transmitting a signal that varies in frequency over a fixed period of time. This provides a measurement of speed and distance. Since the receivers in these radars expect signals with definitive frequency patterns, they can perform more advanced signal cancellation techniques to reduce the effects of interference (including jamming).13 Despite this, there are some forms of interference, such as a chirp or sweep signal, that cannot be isolated,14 resulting in performance degradation in the presence of heavy interference. Due to the limited use of automotive radar, interference is not a problem in today’s environment; however, as automotive radars become more widespread, we expect that interference between automotive radars in different vehicles will become a major issue.
SECURITY RISKS OF DSRC
In 2017, several newly released vehicles will use DSRC technologies to communicate over designated vehicular networks in the U.S. These networks enable mobilized vehicles to exchange data vehicle-to-vehicle (V2V), as well as vehicle-to-infrastructure (V2I), within range. Information such as velocity and global position can be used by V2V applications that leverage DSRC to perform collision prevention and driver assistance tasks, making it extremely important that DSRC devices be reliable and secure. Additionally, V2I applications that use DSRC can provide more convenient e-parking, vehicle safety inspection and toll payment services. In general, DSRC exhibits low network latency, high-reliability, a priority ranking hierarchy and improved security and privacy.15
Current implementations of vehicular communication systems are modeled after existing Wi-Fi communication systems (i.e., IEEE 802.11p, the standard used in DSRC, is a subset of the IEEE 802.11 standard). Thus, in general, DSRC technologies are susceptible to similar types of attacks used against traditional Wi-Fi, which include jamming, spoofing and interference.16 In addition to these attacks, DSRC technologies are also susceptible to attacks on user confidentiality.
Jamming
In contrast to automotive mmWave radar, DSRC systems operate at relatively low frequencies (5.9 GHz), improving the maximum range of detection but making them more susceptible to jamming attacks. Research has shown that constant, random and intelligent jamming attacks can deny service to DSRC applications to the point of disabling their entire functionalities.17 In addition, DSRC may potentially experience denial-of-service attacks designed to jam the system from within the vehicular network, such as malware, spamming and black hole attacks.16 All of these attacks have the potential to disable vehicular communications for extended periods of time, putting a targeted vehicle and its occupants in danger if the vehicle relies on DSRC for collision warning.
To combat potential attacks, considerable research has been conducted to examine solutions such as additional authentication, physical separation of networks within the same vehicle, switching of frequencies when denied service and communication with legitimate DSRC devices to blacklist rogue devices.17-19 Despite these efforts, jamming is still a major security concern due to the ease of carrying out an attack and the potential consequences it has on targeted systems.
Spoofing
Although DSRC is more susceptible to jamming than automotive radar, it exhibits inherent resistance to spoofing attacks. Since DSRC is a subset of the IEEE 802.11 standard, it has a predefined packet sequence that incorporates packet authentication within its packet headers. Because of this, spoofing a DSRC device requires knowledge of the specific sequences used in the packet headers. In addition, the DSRC standard is capable of incorporating public key cryptography during transmission, further improving security.
Despite these advantages, DSRC is still vulnerable to specific types of spoofing attacks. These include attacks from within the network itself and attacks that modify the signals sent throughout the network. If able to determine or obtain the necessary credentials for authentication, then an attacker may be able to impersonate a legitimate device, enabling the transmission of false information.20 In contrast, spoofing attacks such as replay attacks or man-in-the-middle attacks may allow an adversary to modify signal information by intercepting a transmitted signal and retransmitting a slightly modified version of the signal.
Although DSRC technology is ultimately susceptible to spoofing, its inherent robustness due to predefined packet authentication mitigates the severity of this security risk. Furthermore, several supplementary measures can be implemented to provide additional security such as additional authentication.
Interference
DSRC has been allocated a 75 MHz frequency band at 5.9 GHz by the Federal Communications Commission so it does not experience any (legal) interference from non-DSRC devices, such as Wi-Fi operating in the 5 GHz band. Currently, there are relatively few DSRC devices implemented in vehicles on the road; consequently, mutual interference is a non-issue. In the future, however, when DSRC devices become widespread, interference between devices will be a concern, especially in congested environments such as downtown areas. Although current strategies for reducing mutual interference (such as interference cancellation, power and frequency adaptation and improved MAC layer protocol design) can decrease the effect of interference on DSRC, mutual interference is still a notable security concern that has yet to be completely addressed. 21,22
Confidentiality
In addition to jamming, spoofing and interference, DSRC devices must also address the issue of confidentiality due to its nature as a communications system. Not only do DSRC devices need to maintain information privacy, but they also need to ensure that unwanted third-parties cannot covertly track the location of the device over an extended period of time. Potential threats to confidentiality include eavesdropping, masquerading and traffic analysis.23
Although the consequences of failing to address information and location privacy are not as severe as those due to jamming, spoofing and interference, maintaining confidentiality in vehicular networks is one of the more discussed security topics. This is due to the exceptionally low complexity of conducting an attack. For naïve DSRC technologies, such attacks can be performed by just listening to the data transmissions within a network and analyzing the traffic.
Furthermore, even if the data itself is encrypted, modern traffic analysis techniques can examine traffic patterns of a specific device and extract location information from the analysis. As a result, DSRC technologies need to be designed intelligently in order to prevent attacks on confidentiality. Currently, there are various measures such as device cloaking; however, these solutions introduce considerable complexity to the entire network and are, therefore, sometimes undesirable.
COMPARING AUTOMOTIVE RADAR AND DSRC SECURITY
Both automotive radar and DSRC technologies have inherent security flaws as summarized in Table 1. “High” indicates a security risk with a high potential for major consequences, “moderate” indicates a security risk with a moderate potential for major consequences or a high potential for minor consequences, “low” indicates a security risk with a small potential for both major and minor consequences and “none” indicates no security risk.
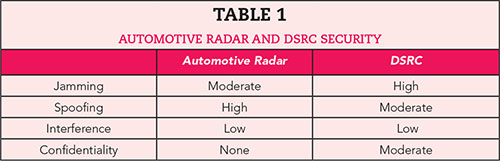
On the one hand, DSRC devices are more susceptible to jamming than automotive radars since they are subject to jamming attacks from within the vehicular network. On the other hand, automotive radars are considerably more susceptible to spoofing attacks than DSRC technologies due to their lack of signal verification. Currently, both automotive radar and DSRC devices are not significantly impacted by interference. In the future, when the technologies become more widespread, interference will become an important security concern.
In addition, DSRC technology must account for attacks on confidentiality due to its nature as a communications system. Overall, although there are more types of attacks for DSRC systems, DSRC is more secure than automotive radar due to its built-in security mechanisms and its ability to communicate with other legitimate DSRC sources. This does not mean that DSRC equivalents can replace automotive radar, since the functionalities of both technologies are crucial for a variety of vehicular applications.
At The University of Texas at Austin, we are performing research on joint radar and communication. One line of research is to fuse information derived from separate radar and DSRC modules. This has been shown to improve target localization.24,25 In addition, a joint system is not solely dependent on a single factor, such as sensor quality or degree of noise. Furthermore, while the DSRC aspect of the system remains the same, the radar aspect receives an extra layer of authentication, dramatically reducing the device’s vulnerability to a spoofing attack. Joint radar and communications devices operate using the same signal or different time/frequency resources, which does not increase system mutual interference.
One of our primary areas of research is how to incorporate a communications waveform (e.g., IEEE 802.11ad) and its inherent security into the signal structure of automotive radar.2 By exploiting special data sequences within the IEEE 802.11ad signal structure, radar parameter estimation for both range and velocity detection can be performed with high accuracy. This framework enables joint long-range automotive radar and V2V communication at 60 GHz, improving detection accuracy and reliability.
Another primary area of research is in the development of a cost-effective microwave IEEE 802.11p radar that may be used in tandem with mmWave automotive radars to perform a security check with the received radar waveform.25 By exploiting a special characteristic of the IEEE 802.11 channel energy, range detection using a communications waveform at microwave frequencies can be performed at meter-level accuracy. The main advantage of performing radar tasks at microwave frequencies is the significantly reduced cost and increased availability of microwave equipment. In addition, by supporting high-accuracy mmWave automotive radars with a joint microwave radar and communications system, the security issues associated with automotive radar (e.g., spoofing) can be eliminated.
HACKING A VEHICLE
In 2014, security researchers published a paper describing a strategy for a remote automotive attack at an international hacker convention.26 A year later, they took a step further and demonstrated a wireless attack on a Chrysler Jeep being driven on a public highway, posting the footage as a YouTube video.27 By exploiting a major oversight in Chrysler’s network design, they were able to brute force their way into the system and exploit the Linux operating system. From there, they were able to remotely control steering at low speeds, engine status, the air conditioning system and radio from the Internet.
The public reacted quite negatively towards this demonstration. Their angry complaints prompted several changes in the automotive industry, one of them being the release of a best practices paper by Intel (McAfee)28 outlining all the known ways vehicles can be hacked and the most effective countermeasures, including but not limited to attacks from wireless V2V and V2I receivers, Bluetooth systems and the engine control unit.
Despite the paranoia caused by the video, wireless malicious hacking of a vehicle has been virtually nonexistent. Though the idea has been popularized in movies (such as Disney’s® “Tron”) or video games (such as Ubisoft’s® “Watch Dogs”), there has only been one documented instance of malicious hacking of a car. In 2010, an angry former employee bricked hundreds of cars at a dealership,29,30 destroying several million dollars’ worth of cars, but injuring no one in the process. Additionally, although Miller and Valasek26 provided a substantial list of vehicle models susceptible to the same type of attack they performed, there have been no reported attacks on any of these vehicles.
This recent public outburst can be explained by the heavy consequences of allowing vulnerable vehicles to drive on public roads. Although the threat of hacking vehicles is real, with the proper precautions these threats can be avoided. Like any other networking protocol, vehicular networks will always be subject to attack. But as long as security concerns are addressed in an ethical, appropriate and timely manner, there is no reason to prevent or delay the integration of communication networks in vehicles.
CONCLUSION
As automotive radar and vehicular networks grow more and more widespread, it is crucial that the security risks of each technology are examined and addressed. Automotive radar and DSRC technology both exhibit inherent security flaws, motivating the development of a joint radar and communications system. In addition, a documented instance and demonstration of hacking a vehicle on the road has greatly increased public awareness of the topic. Although the security breach demonstrated was not due to the flaws of automotive radar or DSRC technology, it more than sufficiently demonstrated the potential of an attack that can result in severe consequences.
To perform many of the attacks introduced in this paper, attackers need only to attach a device that can intercept and/or scan a signal to a centralized computer, and in some cases, a signal generator and transmitter. Some of the more complicated attacks discussed (such as spoofing a DSRC device) may require more sophisticated equipment that enables the attacker to gain access to well-protected information. As a result, the majority of malicious hackers will likely seek a simplistic security breach that allows them to gain considerable access, similar to the Chrysler Jeep hacking demonstration.
Due to cost and complexity, many hackers will likely avoid attacking a vehicular system using a sophisticated strategy. As black hat research advances, however, conducting spoofing attacks on automotive radar will become more and more feasible, encouraging more malicious hackers to consider spoofing and dramatically increasing the risks associated with unprotected devices in vehicular environments. The observations presented in this paper should be considered as a sober warning to automobile companies, motivating them to address the security risks of both automotive radar and DSRC technologies as soon as possible.
References
- R. Heath Jr., “MIMO at Millimeter Wave,” http://web.stanford.edu/~apaulraj/workshop70/pdf/mmWaveMIMO_Heath.pdf, 2015.
- P. Kumari, N. G. Prelcic and R. W. Heath Jr., “Investigating the IEEE 802.11ad Standard for Millimeter Wave Automotive Radar,” Proceedings of the Vehicular Technology Conference, September 2015.
- N. Currie and C. Brown, “Principles and Applications of Millimeter-wave Radar,” Artech House, 1987.
- “Millimeter Wave Radar Brings International Recognition,” www.gtri.gatech.edu/history/innovations/millimeter-wave-radar-brings-international-recognition, 2011.
- N. Li and Y. Zhang, “A Survey of Radar ECM and ECCM,” IEEE Transactions on Aerospace and Electronic Systems, Vol. 31, No. 3, August 1995, pp. 1110–1120.
- S. Janusas, “Monopulse Radar Jammer Using Millimeter Wave Techniques,” U.S. Patent 5,200,753. April 6, 1993.
- X. Qiao, T. Jin, X. Qi, M. Zhang, S. Yuan and Q. Zhang, “Anti-Millimeter Wave Polarization Agile Active Jamming,” Proceedings of the International Conference on Microwave and Millimeter Wave Technology, April 2007, pp. 1–4.
- W. Zhang, H. Zeng, Y. Li and X. Wang, “Polarimetric Radar Performance Test of Signal Processing for Anti-Active Jamming,” IET International Radar Conference, May 2009, pp. 1–4.
- V. Richard, “Millimeter Wave Radar Applications to Weapons Systems,” USA Ballistic Research Laboratories, Final Report, June 1976, pp. 1–124.
- R. Chauhan, “A Platform for False Data Injection in Frequency Modulated Continuous Wave Radar,” http://digitalcommons.usu.edu/cgi/viewcontent.cgi?article=4983&context=etd, 2014.
- S. Roome, “Digital Radio Frequency Memory,” Electronics & Communication Engineering Journal, Vol. 2, No. 4, September 1990, pp. 147–153.
- J. Zhao, G. Zucchelli and M. Roggero, “Design of FMCW Radars for Active Safety Applications,” http://embedded-computing.com/articles/design-fmcw-radars-active-safety-applications/2015.
- A. Stove, “Linear FMCW Radar Techniques,” IEEE Proceedings F Radar and Signal Processing, Vol. 139, No. 5, November 1992, pp. 343–350.
- M. Brooker, “Mutual Interference of Millimeter-Wave Radar Systems,” IEEE Transactions on Electromagnetic Compatibility, Vol. 49, No. 1, March 2007, pp. 170–181.
- “DSRC: The Future of Safer Driving,” www.its.dot.gov/factsheets/dsrc_factsheet.htm, 2015.
- C. Laurendeau and M. Barbeau, “Threats to Security in DSRC/WAVE,” Proceedings of the 5th International Conference on Ad-Hoc Networks & Wireless, August 2006, pp. 266–279.
- A. Serageldin, H. Alturkostani and A. Krings, “On the Reliability of DSRC Safety Applications: A Case of Jamming,” International Conference on Connected Vehicles and Expo, December 2013, pp. 501–506.
- T. Zhang, H. Antunes and S. Aggarwal, “Defending Connected Vehicles Against Malware: Challenges and a Solution Framework,” IEEE Transactions on Industrial Technology, Vol. 1, No. 1, February 2014, pp. 10–21.
- H. Hasbullah, I. Soomro and J. Ab Manan, “Denial of Service (DOS) Attack and its Possible Solutions in VANET,” International Journal of Electrical, Computer, Energetic, Electronic and Communication Engineering, Vol. 4, No. 5, May 2010, pp. 813–817.
- E. Hamida, H. Noura and W. Znaidi, “Security of Cooperative Intelligent Transport Systems: Standards, Threats Analysis and Cryptographic Countermeasures,” Electronics, Vol. 4, No. 3, July 2015, pp. 380–423.
- S. Maddio, A. Cidronali, M. Passafiume, G. Collodi and G. Manes, “Interference Cancellation for the Coexistence of 5.8 GHz DSRC and 5.9 GHz ETSI ITS,” IEEE MTT-S International Conference on Microwaves for Intelligent Mobility, April 2015, pp. 1–4.
- Q. Xu, T. Mak, J. Ko and R. Sengupta, “Vehicle-to-Vehicle Safety Messaging in DSRC,” Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks, September 2004, pp. 19–28.
- Information Resources Management Association, “Transportation Systems and Engineering: Concepts, Methodologies, Tools, and Applications,” IGI Global, 2015.
- Q. Chen, T. Roth, T. Yuan, J. Breu, F. Kuhnt, M. Zollner, M. Bogdanovic, C. Weiss, J. Hillenbrand and A. Gern, “DSRC and Radar Object Matching for Cooperative Driver Assistance Systems,” IEEE Intelligent Vehicles Symposium, June 2015, pp. 1348–1354.
- E. Yeh, R. Daniels and R. Heath, Jr., “Forward Collision Vehicular RADAR with IEEE 802.11: Feasibility Demonstration Through Measurements,” in preparation, 2016.
- C. Miller and C. Valasek, “A Survey of Remote Automotive Attack Surfaces,” DEF CON, 2014.
- A. Greenberg, “Hackers Remotely Kill a Jeep on the Highway-With Me In,” www.youtube.com/watch?v=MK0SrxBC1xs, 2015.
- “Automotive Security: Best Practices: Recommendations for Security and Privacy in the Era of the Next-Generation Car,” http://www.mcafee.com/us/resources/white-papers/wp-automotive-security.pdf, 2015.
- K. Poulsen, “Hacker Disables More Than 100 Cars Remotely,” Wired, www.wired.com/2010/03/hacker-bricks-cars/.
- J. Hirsch, “Hackers Can Now Hitch a Ride on Car Computers,” www.latimes.com/business/autos/la-fi-hy-car-hacking-20150914-story.html, 2015.

Enoch Yeh is a graduate student in the Wireless Networking and Communications Group in the Electrical and Computer Engineering Department of the University of Texas at Austin. He completed his B.S. in electrical engineering from UT Austin in 2014. His research interests include wireless communications, communications and radar in vehicular networks and wireless networking.

Junil Choi received his B.S. and M.S. degrees in electrical engineering from Seoul National University in 2005 and 2007, respectively, and his Ph.D. degree in electrical and computer engineering from Purdue University in 2015. He is now with the department of electrical engineering at POSTECH as an assistant professor. From 2007 to 2011, he was a member of technical staff at Samsung Electronics in Korea. Before joining POSTECH, he was a postdoctoral fellow at The University of Texas at Austin.

Nuria Gonzalez-Prelcic is an associate professor at the University of Vigo, Spain and has held a visiting positions with The University of Texas at Austin (2014 and 2015). Her main research interests include signal processing theory and signal processing for wireless communications: filter banks, compressive sampling and estimation and MIMO processing for millimeter wave communications. She is currently the head of AtlantTIC, Research Center on ICT at the University of Vigo.

Dr. Chandra R. Bhat is the director of the Center for Transportation Research (CTR) and the Adnan Abou-Ayyash Centennial Professor in Transportation Engineering at The University of Texas at Austin, where he has a joint appointment between the Department of Civil, Architectural and Environmental Engineering (CAEE) and the Department of Economics. Bhat is a world-renowned expert in the area of transportation and urban policy design, with far reaching implications for public health, energy dependence, greenhouse gas emissions and societal quality of life.

Robert W. Heath Jr. is a Cullen Trust Endowed Professor in the Department of Electrical and Computer Engineering at the University of Texas at Austin and a member of the Wireless Networking and Communications Group. He received his Ph.D. in electrical engineering from Stanford University. He is a co-author of the book “Millimeter Wave Wireless.” His current research interests include millimeter wave for 5G, cellular system analysis, communication with low-resolution ADCs and vehicle-to-X systems.
