Radio frequency identification (RFID) is an automatic identification method that relies on storing and remotely retrieving data using devices known as RFID tags or transponders. RFID systems with a variety of radio frequencies and techniques have been introduced.1 Among them, the ultra-high frequency (UHF) band passive RFID system has drawn a great deal of attention because of its numerous benefits, such as cost, size and increased interrogation range. In particular, the interrogation range of the UHF RFID system is comparatively large, due to the use of a traveling electromagnetic (EM) wave to transfer power and data. The increased interrogation range makes it possible for RFID to revolutionize various commercial applications, such as supply chain management.1,2 Moreover, the interrogation range has been considered as the most important feature representing the performance of a UHF RFID system.
The interrogation range is similar to cell coverage in wireless communication systems. In general, there are many factors involved in limiting the interrogation range. Among these, three major factors are the power required to turn on a tag’s integrated circuit (IC) chip, the reader receiver’s sensitivity and the wave propagation environment. Propagation environment is an extrinsic parameter affecting the interrogation range, whereas the power to turn on a tag’s chip and the reader receiver’s sensitivity are considered as intrinsic parameters. These two intrinsic parameters are closely related to the powers of signal and noise in RFID links. Therefore, this power relationship can be easily calculated using the link budget, which is the wireless communication system designer’s primary tool for estimating the cell coverage.
Similarly, the link budget analysis is also applicable to an RFID case. However, a UHF RFID system differs from conventional wireless communication systems in the link budget analysis. This is because the tag has no internal power supply and the reader must supply the power. Consequently, the link budget is mainly dependent on the threshold power necessary to power up the tag.3-5 Another major difference is that the phase noise of the transmission (TX) leakage at the reader’s circulator has greater influence on the system noise than the thermal noise at the reader’s receiver.6-8 In this article, link budget calculations, considering the intrinsic characteristics of UHF RFID systems, are presented to provide guidance regarding system design and deployment.
RFID Radio Links

Figure 1 Comparison between a conventional system and a UHF RFID system.
It is well known that a communication link encompasses the entire communications path from the transmitter, through the propagation channel and up to the receiver. In a typical wireless communication system, illustrated in Figure 1, there are forward and reverse links. The forward link is the communication link from a base station (BS) to a mobile station (MS), whereas the reverse link is the opposite communication link, from MS to BS. Because BS and MS can simultaneously transmit data to each other through the forward and reverse links, a conventional communication link is called full duplex. In addition, conventional wireless systems usually maintain a link balance between forward and reverse links, where the power levels of the two links have little difference. Therefore, the forward link coverage is almost the same as that of the reverse link, although the transmit power and sensitivity of both links are a little different.
On the other hand, RFID links, as illustrated, are different from conventional wireless links. A typical RFID system is composed of two components: a reader and a tag. The reader, sometimes called the interrogator, is made up of a transmitter/receiver module with one or more antennas. The tag consists of a microchip for storing data and an antenna to transmit stored data. Tags are normally categorized into active and passive types by the presence or absence of an internal power supply. Because tags have no power supply of their own in passive RFID systems, they obtain energy from the continuous wave (CW) signals transmitted by a reader. In addition, passive tags transmit their data only by backscatter modulation. In other words, the data transmission from tags to the reader is done by reflecting the wave energy back to the reader.9 Therefore, an RFID link is half duplex: reader to tag and then tag to reader. This means that RFID links are intrinsically unbalanced. Moreover, the reverse links are highly correlated to the forward link, because the tag’s transmit power is determined by the reader’s transmit power.
Forward Link Maximum Allowable Loss
In the forward link, the forward maximum allowable loss is mainly determined by the tag characteristics. For example, let the minimum threshold power necessary to power up the chip be Pth. Then the forward maximum allowable loss in dB, Lƒ, max, can be calculated as
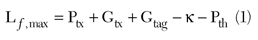
where
Ptx (dBm)=the transmit signal power fed into the reader antenna;
Gtx (dBi)=the reader’s transmit antenna gain;
Gtag (dBi)=the tag antenna gain;
κ(dB)=the power loss due to backscatter modulation; and
Pth (dBm)=the threshold power necessary to power up the chip.
In passive RFID systems, the power induced at the tag’s antenna is divided into two parts: one for the chip’s power supply and the other for backscatter. The term κ refers to power loss due to backscatter modulation, which can be characterized by the tag modulation schemes: amplitude shift keying (ASK) or phase shift keying (PSK).10 This power loss is then easily derived according to the following equation:
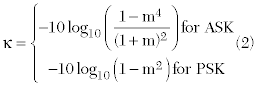
where 0

Figure 2 Forward link budget calculations.
Figure 2 depicts the conceptual link budget calculation in the forward link. Upward direction arrows indicate gains, while downward direction arrows indicate losses. The tag received power, Ptag-rx, should be greater than Pth, to turn on the tag’s IC chip. Accordingly, the maximum allowable path loss is calculated by Equation 1.
Reverse Link Maximum Allowable Loss
In the reverse link, the backscattered signal from the tag should be strong enough to meet the minimum signal-to-noise ratio (SNR) requirement at the reader’s demodulation output. This is very similar to general wireless communication system links. However, because the CW signal always exists in a reverse link to turn the tag on, the TX leakage level plays an important role in determining the reverse link interrogation range. Fortunately, the direct current (DC) offset due to TX leakage is removed from a baseband bandpass filter. Nonetheless, the phase noise of the TX leakage on the receiving bandwidth is, unfortunately, not removed by the filter and may be much stronger than the thermal noise, to a degree that the reverse link interrogation range mainly depends on the phase noise of the TX leakage. On the other hand, in a general wireless communication system, the phase noise of the TX leakage is normally not a major problem, because duplexing techniques, such as frequency division duplexing (FDD) and time division duplexing (TDD), are applied.

Figure 3 UHF RFID system reader architecture.
To calculate the phase noise power of the TX leakage signal, the reader architecture should be given first. Consider the direct-conversion receiver architecture shown in Figure 3. The reader is composed of a local oscillator (LO), a transmitter, a receiver and an antenna. The antenna can be configured in two types, two antennas or one antenna with a circulator, as shown in the figure. The circulator is a non-reciprocal three-port device, where the signals travel from the transmitter port to the antenna port or from the antenna port to the receiving port. In practice, the circulator cannot isolate the transmitter from the receiver entirely, due to the inherent leakage between its ports. Generally, TX leakage is between -20 to -50 dB.11

Figure 4 Reverse link budget calculations.
In the reverse link, the tag receives a CW signal from the reader transmit antenna, modulates it and backscatters a portion of it back to the reader receive antenna, as shown in Figure 4. Using the monostatic radar equation defined by Balanis,12 the reverse maximum allowable loss in dB, Lr, max, can be calculated as
Lr,max = (Ptx + Gtx + 2Gtag + Grx - Γ -
NF - SNRmin - Npn - N)/2 (3)
where
Γ (dB) = the power reflection loss;
NF (dB) = the noise figure;
SNRmin (dB) = the minimal SNR to meet a given per-formance requirement;
N (dBm) = the thermal noise power; and
Npn (dBm) = the phase noise power of TX leakage.
The power reflection loss due to the ion factor is given as
Γ = 10 log10(m2) (4)
for both ASK and PSK.
To calculate the reverse link budget, the minimum SNR value and the phase noise of the TX leakage power should be known. They are considered in the following sections. The minimum SNR value is obtained from the symbol error rate analysis of a system, and the phase noise of the TX leakage is obtained by integrating the power spectral density (PSD) over the passband of a baseband filter.
Phase Noise of the TX Leakage
The phase noise is the degree of the LO’s spectral impurity or a measure of the imperfection of the sinusoidal wave. If the PSD of a TX leakage is known, it is possible to calculate the phase noise level of the TX leakage by numerically integrating a PSD within the receiver’s passband.
The LO provides two identical frequency signals: one for the transmitter and the other for the receiver. Neglecting the amplitude noise, the LO signal can be expressed as
XLO(t) = ALO cos[ωt + θLO(t)] (5)
where
ALO = the amplitude of the LO signal,
ω = the angular frequency, and
θLO(t) = the phase noise of the LO signal.
The power amplifier (PA) amplifies the LO signal to achieve a high power level. The amplified signal feeds into the reader antenna via the circulator and then radiates into the air. Simultaneously, the reader antenna also receives the backscattered signals from the tag. The circulator cannot totally isolate the transmitter from the receiver due to the inherent leakage between its ports. The TX leakage signal is delayed by Δt and is given as follows
XU(t) = AU cos[ω(t - Δt) + θLO(t - Δt)] (6)
where
AU= the signal amplitude
the signal amplitude
η = the TX leakage level
Δ = the round-trip delay between the TX leakage and the LO signal.
Before further discussion, it is important to recognize that θLO(t), in Equations 5 and 6, is related to the phase noise from the same LO except for a time delay.
Here, it is assumed that the baseband bandpass filter used in the reader receiver has a sharp frequency selectivity. To simplify the forthcoming analysis, the impulse response of the bandpass filter is characterized approximately with an ideal rectangular transfer function and its low-end frequency and high-end cut-off frequency are denoted as ƒL andƒH, respectively. With a quadrature receiver, the TX leakage signal (Equation 6) and the LO signal (Equation 5) are mixed and the output is low-pass filtered. The resulting phase noise of the TX leakage signal will then be given as follows
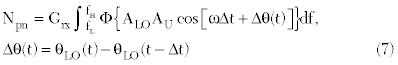
where Grx is the transfer coefficient of the receiver, taking into consideration the total gain of the RF circuits and Φ{·} denotes the operation of calculating the PSD of a random process, that is the Fourier transform of the auto-correlation function of a random process. If the RFID transmits only a UHF band CW signal, then the Npn varies dramatically with a time delay. In the worst case, ωΔt takes a value of (2n-1)π/2 in Equation 7, where n is a positive integer, and the maximum phase noise of the TX leakage can be approximately expressed as
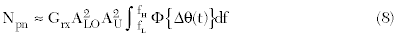
which gives a maximum phase noise of the RFID reader.
If the same LO is used for the transmit and receive operations, the phase noise of the received signal is correlated with the LO, where the level of correlation depends on the time difference between the two signals. If the time difference is short, the corresponding effect greatly abbreviates the phase noise spectrum at the baseband. In radar applications, such as RFID, this phase-noise-reducing effect is called range correlation.6,7 The baseband PSD at the offset frequency Δƒc with a round-trip delay of Δt is given by6
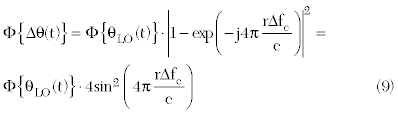
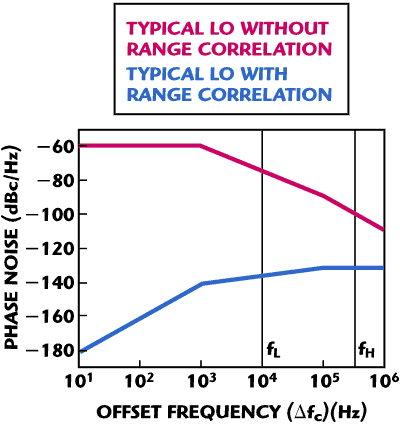
Figure 5 LO phase noise vs. offset frequency.
Figure 5 shows an example of a typical PSD of the LO itself and the phase noise reduction effects due to the range correlation with a round-trip delay of 1 m. The typical PSD of the LO is selected considering state-of-the-art UHF RFID LO performance. The effect of the range correlation on the phase noise for different offset frequencies was estimated using Equation 8. For example, with an offset frequency of 10 Hz, the phase noise is reduced by 130 dB. The phase noise reduction is proportional to the square of the round-trip delay r and the square of the offset frequency, Δƒc. Due to the short round-trip delay (less than 1 m) between the TX leakage and the LO signals, the phase noise effects are dramatically reduced relative to the tag backscattered signal.

Table 1 Phase Noise Power Reduction Due to Range Correlation (4 W EIRP)
The phase noise reduction effect due to range correlation depends on the filter bandwidth. For a 160 kbps data rate, the measured phase noise reduction values have been shown previously.13 The measured value is 41 dB and is almost the same as the result obtained by the authors. As shown in Table 1, the TX leakage noise is much stronger than the thermal noise, to such a degree that the maximum allowable path loss mainly depends on the TX leakage level. In addition, the assumption that the phase noise of the TX leakage is dominant in determining the reverse link budget is verified. For a closed-loop phase-locked loop (PLL), the PSD of the phase noise is filtered by the transfer function of the PLL, and the phase noise effects are even smaller. Thus, this result for the open loop voltage-controlled oscillator (VCO) represents the worst case.
Minimum SNR
Reader sensitivity is an important parameter that defines the minimum level of the tag signal detected by a reader receiver.14 The reader sensitivity is usually defined with respect to a certain signal-to-noise ratio (SNR) at the receiver. SNR is also obtained by a required transmission quality: bit error rate (BER) or symbol error rate (SER). A high SNR guarantees a low transmission error rate, but a large transmission power is required. Therefore, the minimum SNR value to meet a required transmission quality is preferable to enhance reader sensitivity.
The factors that can affect reader sensitivity include receiver implementation details, communication protocol specifics and noise, including interference from other readers. For example, according to the encoding scheme, the minimum SNR to meet a given BER can be found by different error probability equations. The minimum SNRs can be found by solving the following equations for a given BER value.
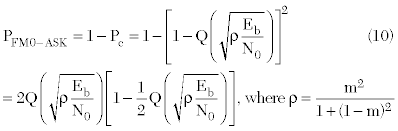
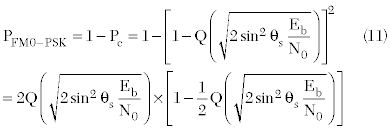
where
Pe=the error probability
Pc=the probability of a correct decision
θs=the modulation phase angle in a PSK
Eb=bit per energy
N0=the power spectral density of additive white Gaussian noise.

Figure 6 Bit error rate for ASK and PSK modulation.
Using Equations 10 and 11, the BER results for ASK and PSK modulation are given in Figure 6. In the ASK case, as m is increased, the BER is decreased. In the PSK case, Δθ=π/4 shows better BER performance. At a BER of 10-3, the minimum required SNRs are 10 dB for m=1, 12 dB for m=0.8 and 15 dB for m=0.6.
Link Budget Calculations
To show the usefulness of the link budget analysis, two different cases are presented: a stationary reader case and a mobile reader case. In the mobile RFID case, which uses an internal antenna and a low performance circulator due to size limitations, the antenna gain is -3 dBi, and the circulator performance may be very low. The TX powers are 1 W in the stationary reader and 0.2 W in the mobile reader. In calculating the interrogation range, the used path loss model is the free space model. The interrogation range is easily calculated from the maximum allowable loss and the path loss model.

Table 2 Link Budget Results
The resulting link budget is given in Table 2. Case I shows that the interrogation range in the forward link is smaller than that in the reverse link, which means that stationary RFID is a forward link limited system. Case II shows the opposite result: a mobile RFID is a reverse link limited system. The prominent difference between the two cases is the phase noise of the TX leakage. In case II, therefore, TX leakage should be reduced to overcome the reverse link limit, because a mobile RFID reader similar to that in case II has poor TX/RX isolation, which results in an increase of phase noise. For the same effective isolated radiation power (EIRP), an antenna with a larger gain is preferable for the reader. This can also reduce the phase noise of TX leakage.
If one of the interrogation ranges is much larger than the other, the system might waste some resources. Therefore, to avoid a waste of resources, it is preferable to balance the two interrogation ranges. An easy way to increase the forward link interrogation range (FIR) is to allocate a large amount of TX power for the forward link. This results in an increased TX leakage, which reduces the reverse interrogation range (RIR) and may cause a reverse link limited system. Therefore, simply increasing transmit power cannot always balance FIR and RIR. In such case, the above link budget analysis can be a useful tool that enables FIR to coincide with RIR within an allowable range.

Figure 7 Determination of interrogation range.
Finally, Figure 7 shows a link budget according to tag-reader distance. The forward link interrogation range (FIR) is defined as the maximum distance at which the tag receives just enough power to turn on, and the reverse interrogation range (RIR) is the maximum distance at which the tag signal meets the minimum reader sensitivity condition. As shown, the FIR is determined by a tag threshold voltage, and the reverse link interrogation range (RIR) is mainly determined by the TX leakage noise level.
Conclusion
When system engineers are deploying UHF RFID systems, the interrogation range is a key design parameter. To maintain good performance and stable operation of an RFID system, the interrogation range should first be well understood in relation to the link budget. In this regard, a link budget analysis for UHF RFID systems has been presented in this article. A forward link budget was calculated using the required power at the input of the tag IC chip, while a reverse link budget was calculated from the required SNR at the demodulator output of the reader to detect the receiving tag’s data correctly.
As an example of link budget calculation, stationary RFID reader and mobile RFID reader results were compared. In the stationary reader case, the FIR is less than the RIR and in the mobile reader case, RIR is less than FIR. Therefore, the stationary RFID reader case can be described as a forward link limited system, whereas the mobile RFID reader case can be described as a reverse link limited system. Since the threshold power necessary to power up the tag is the dominant factor determining FIR, it is a bottleneck in the stationary RFID. Similarly, the phase noise of TX leakage is a bottleneck in the mobile RFID. The results presented here can serve as a useful reference when deploying UHF RFID systems.
References
1. R. Weistein, “RFID: A Technical Overview and its Application to the Enterprise,” IEEE IT Professional, Vol. 7, No. 3, May/June, 2005, pp. 27-33.
2. Y. Bendavid, S.F. Wamba and L.A. Lefebvre, “Proof of Concept of an RFID-enabled Supply Chain in a B2B E-commerce Environment,” 2006 Int’l Conference on Electronic Commerce (ICEC’06) Proceedings, pp. 564-568.
3. U. Karthaus and M. Fischer, “Fully Integrated Passive UHF RFID Transponder IC with 16.7-mW Minimum RF Input Power,” IEEE Journal of Solid-State Circuits, Vol. 38, No. 10, October 2003, pp. 1602-1608.
4. J.P. Curty, N. Joehl, C. Dehollain and M.J. Declerq, “Remotely Powered Addressable UHF RFID Integrated System,” IEEE Journal of Solid-State Circuits, Vol. 40, No. 11, November 2005, pp. 2193-2202.
5. P.V. Nikitin, K.V. Rao, S.F. Lam, V. Pillai, R. Martinez and H. Heinrich, “Power Reflection Coefficient Analysis for Complex Impedances in RFID Tag Design,” IEEE Trans. on Microwave Theory and Techniques, Vol. 53, No. 9, September 2005, pp. 2721-2725.
6. G. De Vita and G. Iannaccone, “Design Criteria for the RF Section of UHF and Microwave Passive RFID Transponders,” IEEE Trans. on Microwave Theory and Techniques, Vol. 53, No. 9, September 2005, pp. 2978-2990.
7. A.D. Droitcour, O. Boric-Lubecke, V.M. Lubecke, J. Lin and G.T.A. Kovac, “Range Correlation and I/Q Performance Benefits in Single-chip Silicon Doppler Radars for Non-contact Cardiopulmonary Monitoring,” IEEE Trans. on Microwave Theory and Techniques, Vol. 52, No. 3, March 2004, pp. 838-848.
8. J.H. Bae, J.C. Kim, B.W. Jeon, J.W. Jung, J.S. Park, B.J. Jang, H.R. Oh, Y.J. Moon and Y.R. Seong, “Analysis of Phase Noise Requirements on Local Oscillator for RFID System Considering Range Correlation,” 2007 European Microwave Conference Proceedings, pp. 1664-1667.
9. K. Finkenzeller, RFID Handbook Second Edition, John Wiley & Sons Inc., New York, NY, 2003.
10. EPCglobal Inc., “M Radio-frequency Identity Protocols Class-1 Generation-2 UHF RFID Protocol for Communications at 860 to 960 MHz,” Version 1.0.9, January 2005.
11. W.K. Kim, M.Q. Lee, J.H. Kim, H.S. Lim, J.W. Yu, B.J. Jang and J.S. Park, “A Passive Circulator for RFID Application with High Isolation Using a Directional Coupler,” 2006 European Microwave Conference Proceedings, pp. 196-199.
12. C.A. Balanis, Antenna Theory: Analysis and Design, Second Edition, John Wiley & Sons Inc., New York, NY, 1997.
13. Z.G. Fan, S. Qiao, J.T. Huangfu and L.X. Ran, “Signal Descriptions and Formulations for Long-range UHF RFID Readers,” Progress in Electromagnetics Research, PIER 71, 2007, pp. 109-127.
14. P.V. Nikitin and K.V.S. Rao, “Performance Limitations of Passive UHF RFID Systems,” 2006 IEEE Antennas and Propagation Society Symposium Digest, pp. 1011-1014.
