Abstract
Military Communications, particularly radios and unmanned system radios, continue to be driven towards wider bandwidth, reduced size, weight and power (SWaP) and more dynamic access to the available spectrum. However, a key component that must also be enhanced, to maximize operational effectiveness, is communication security. Secure communications are the backbone of any fighting force, and yet in many radios the architecture can be dominated by the security solution, with multiple processors required to maintain separation between the secure and unsecured processing. To achieve the most efficient radios, both the security and the RF technology need to be integrated, but key challenges remain, particularly in secure boot and root of trust.
The Modern Radio
The traditional military radio typically consists of four or five key processing blocks. The RF stage is used to pre-process the received signal from the antenna, providing the appropriate filtering, gain, and frequency conversion. The digitizer stage converts the RF data to and from the digital domain. Within the digital processing a number of dedicated stages are used to perform waveform modulation and demodulation before a cryptographic stage is utilized to manage the security bridge. The final stage of processing is the user interface, which may involve voice codecs or video processing, depending upon the application. In some cases up to five stages of digital processing are used, as shown in Figure 1.
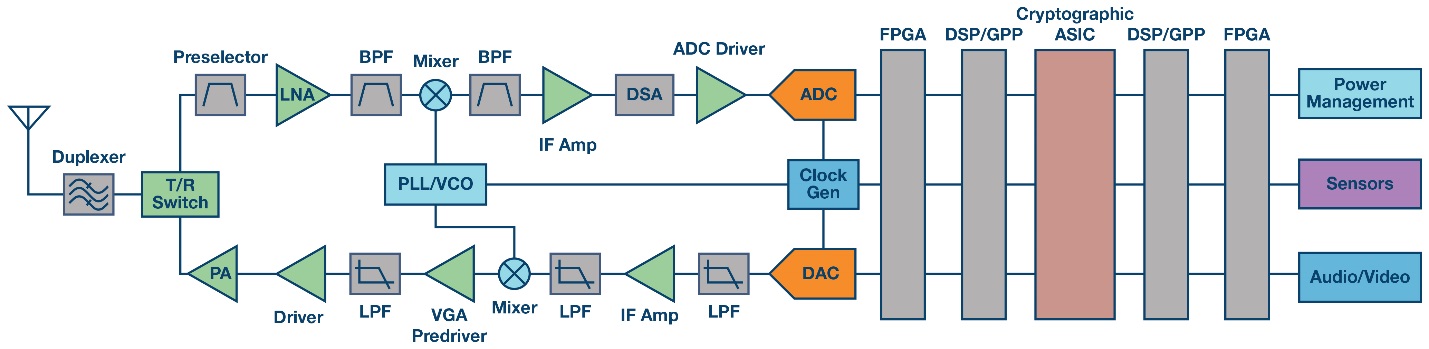
Figure 1 Classical Radio Signal Chain.
Although perfectly functional, the number of processing stages can make radios seem cumbersome. In recent years the focus has been on reducing the discrete components in the RF stages through integration as well as moving more functionality to the digital domain given the benefits of FPGA processing. FPGA-based processing has been a key enabler over the last two decades for software defined radios, particularly given the dedicated processor blocks in the FPGA fabric. FPGAs have provided run-time configurable, upgradeable and more modular architectures. However, given the security challenges, there are still limitations to the architecture. For example, a cryptographic processor requires a multi-processor solution, which limits any possible SWaP reduction.
In recent years, there has been a revolution in new technologies and the integration of RF and digitizer solutions. New direct-conversion RF transceiver devices have provided single device solutions for the RF signal chain, integrating LNAs, I/Q modulators and demodulators, PLLs, ADCs and DACs. The use of direct conversion was enabled through embedded calibration and the quadrature error correction (QEC) algorithm, which overcame the limitation or concerns of using this architecture over super heterodyne solutions of the past. Alternatively, new high speed converters are now able to directly sample or generate waveforms in the RF domain, many up to 6 GHz and beyond, reducing the signal chain to amplifiers, filters and respective converters.
Integrated Security
Although FPGAs provide further optimization of the signal chain for software defined radios, a new approach is needed for the cryptographic processor and the supporting security infrastructure. Software and firmware-based cryptographic approaches offer a solution to the integration challenge. With this method, the crypto can be collocated with the modulation and demodulation processing, and potentially user functions such as voice or image processing. A reference architecture for a secure processing module is illustrated in Figure 2 and includes the following: Processor/Microcontroller, Protected Execution Memory, Protected Storage, Cryptographic Acceleration, Non-volatile Storage and optionally unprotected execution memory.
Utilizing a soft cryptographic engine has significant benefits beyond integration. For example, different levels of security can be applied by reconfiguring or updating the FPGA image, which mitigates the need for hardware changes. Updates to correct bugs and add features are easily supported. However, common vulnerabilities in embedded systems, which are more concerning when the crypto is collocated with other key processing elements, are the lack of verification of the executable firmware or software and the absence of a trusted mechanism to update. As a result, devices are at risk for malicious code injection/replacement. This can be mitigated through implementation of a secure boot process, which prevents execution of unauthorized firmware or software.
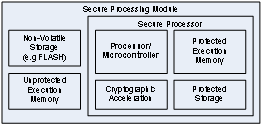
Figure 2 Secure Processing Module Reference Architecture.
Secure boot can be executed on the available processor within the FPGA fabric, such as high performance ARM or soft core Microblaze processors.
Security is built upon foundations, and the secure boot builds layer by layer starting with a root of trust (unchangeable element). The boot ROM will include a decryption algorithm for confidentiality (AES or equivalent), an integrity algorithm (keyed SHA for HMAC or equivalent), and a signature verification algorithm for authentication (RSA or ECDSA). Keys for these algorithms are now provisioned at the FPGA manufacturer in the protected storage regions. For example, the Xilinx Zynq-7000 includes eFUSE and battery backed key registers for this data. The eFUSE and key registers are protected from data extraction and thus provide a basis for secure boot within the FPGA used for all digital signal processing functions.
Additionally, a dedicated non-volatile memory device is also required to store the boot loader. Using a signed configuration file, the boot ROM is instructed to process and instantiate the Boot Loader. The boot ROM verifies the signature of the Boot Loader image. Once validated, the boot ROM decrypts the Boot Loader and verifies the integrity hash. Once decrypted and validated, the Boot Loader is instantiated in protected execution memory and control is passed from the boot ROM to the Boot Loader before handing control to the application.
New Radio Architectures
Utilizing the options identified above, a highly integrated solution is possible. For example, one that provides significant benefits for low power and size constrained applications such as UAVs or man portable systems. An example architecture is depicted in Figure 3.
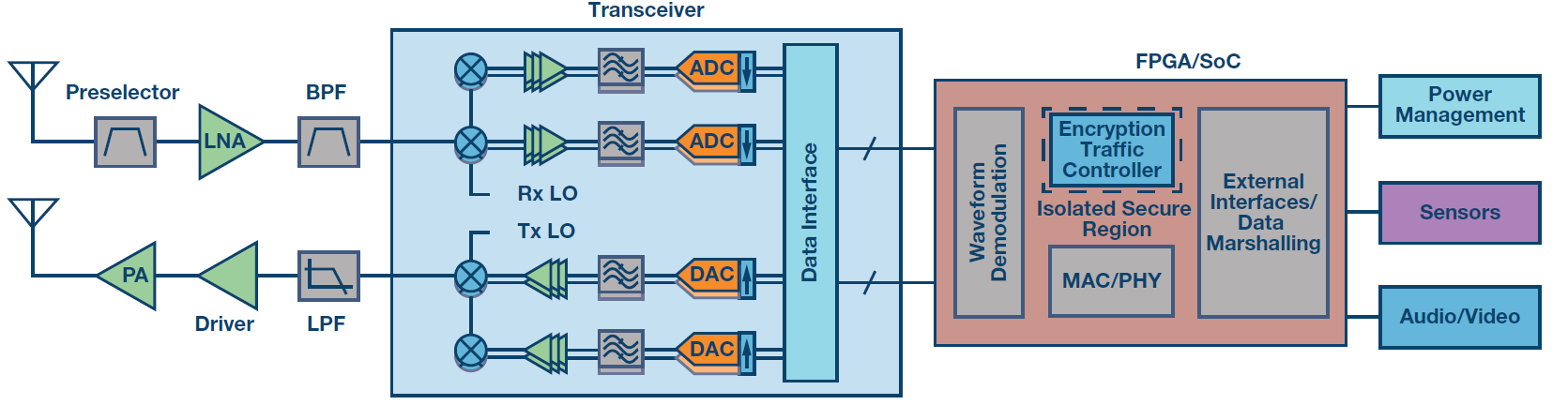
Figure 3 Optimized Radio Architecture.
RF transceivers such as the AD9371 provide an almost complete RF solution with the exception of a Low Noise Amplifier (LNA) and high-power amplifier (HPA). Up to 100 MHz of bandwidth can be processed and provided to the signal processing engines providing low-power, high-linearity data. Using a Xilinx Zynq-7000, user IP can be combined with a firmware- and software-based Sypher™ Cryptographic processing engine, while leveraging secure boot and the foundational trust from the Xilinx FPGAs.
The overall solution reduces the signal chain from potentially two or three dozen active devices to fewer than half a dozen. This decreases size and power while also reducing the complexity and inter-device connections that are often a challenge for system debug and power.
Conclusion
New radio solutions are now reaching unprecedented levels of integration, with RF and digitization processing reduced to one or a handful of devices. The digital signal processing elements are also reaching similar integration levels with the ability of soft security solutions collocated with the waveform and user interfaces. Key elements such as secure boot and secure update, critical in the modern radio, are supported through security provisions in the latest FPGAs and provide the foundation for a holistic secure processing architecture. This results in a scalable approach, with implementation tradeoffs based on data protection levels and desired performance, applicable to a wide variety of applications.
